- Microsoft has seen a new phishing attack vector in nature
- Storm-2372 is stealing access tokens through Microsoft equipment
- The group has been linked to Russia with medium confidence
A new Phishing campaign has been seen using the “device code phishing” through Microsoft equipment to lead governments, NGOs and other industries in Europe, North America, Africa and the Middle East.
The attack, seen by Microsoft himself, takes advantage of the invitations of videoconation meetings of the equipment that incites the victim to enter a device code generated by the attacker that results in the victim to deliver valid access tokens, giving the attacker Access to emails of victims and confidential data.
Microsoft evaluates with an average level of trust that the group, tracked as Storm-2372, is acting in line with Russian tactics and interests.
Data theft and lateral movement
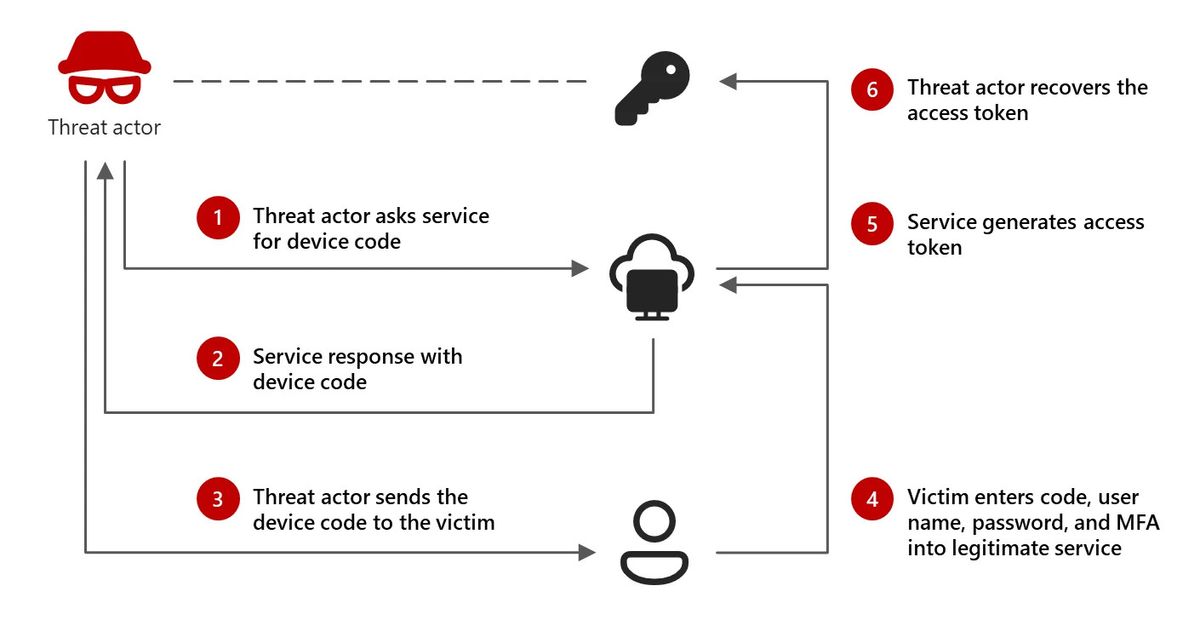
Microsoft says that the threat actor would first build a relationship with the victim through messaging services such as WhatsApp, Signal and Microsoft Teams, positioning itself as an important figure within the victim’s industry. Then, the attacker invites the victim to an online meeting, where the victim is asked to complete a application for authentication of the device code.
The actor will generate a legitimate device code authentication application and then send the code to the victim. The victim enters the code on the legitimate authentication service page that allows the attacker to capture access and update tokens to maintain control over the account.
From there, the attacker will often try to move laterally using the valid access tokens, using a keyword search in the messaging service to harvest confidential data, including username names and passwords, as well as data related to the administrator, TeamViewer, Anydesk, credentials, secret secrets, secrets, ministry and keywords of the government.
The attacker can also use the committed account to send messages or send an email to colleagues with additional phishing messages. Storm-2372 It has also been observed using the specific customer ID for Microsoft’s authentication corridor to request additional tokens that allow the attacker to register their own devices as an authentication device through Enter ID.
To protect against the specific attack vector used by Storm-2372, Microsoft recommends:
- Deactivate the flow of the device code whenever possible.
- Provide Phishing training to all users.
- Revoke access tokens when the activity of Storm-2372 is suspected using revokesigninsiones.
- Enter a policy based on the login risk to block access or force multifactor authentication for high risk signs.
The complete list of defenses and mitigation can be found here.




